Browse our latest articles and resources

Types of Taxes and the Convenience of the Coretax System
Learn about the different types of taxes in Indonesia, their benefits, and how Coretax supports secure, integrated tax reporting.
February 11, 2026
.jpeg)
The New Digital Crime Economy: Why AI-Driven Fraud Syndicates are the 'Startups' of the New Era
AI-powered attacks—such as large-scale deepfake attacks, synthetic identity fraud, and automated device farms—are effectively eroding trad...
February 03, 2026

AI Used for Fraud Detection: How Does It Work?
Fraud is becoming harder to detect with traditional methods. Learn why AI is reshaping how organizations identify and prevent digital fraud...
January 28, 2026

Photo Manipulation: A Hidden Threat Behind Digital Onboarding
The rise of photo manipulation used in digital onboarding. Understand the risks to identity, fraud, and financial security. Let’s take a cl...
January 15, 2026

Hacking: A Real Threat in the Digital Identity Era
Hacking has become a serious risk in the era of AI, deepfake, and modern hacking practices. Understand the definition.
January 12, 2026

Authorized Representative Signatures: Secure and Proper Examples
Not all signatures made on behalf of a representative are legally valid. Learn more about proper signature formats and the risks involved i...
January 03, 2026

Coretax Impersonation: Definition, How It Works, and Security Tips
Coretax impersonation plays an important role in the DJP system. Explore how it works, what it’s used for, and how to use it securely.
January 01, 2026
Invoice vs Receipt: Key Differences and How They’re Used
Don’t get them mixed up! Learn the differences between invoices and receipts, from their definitions and document structure to when each on...
January 01, 2026
Invoice Applications: A Smarter Way to Manage Billing
Still handling invoices manually? Invoice applications simplify digital invoice creation, delivery, and tracking for more efficient billing...
December 31, 2025

How to Create an Invoice: A Complete Guide and Common Mistakes
Need practical tips on creating invoices and invoice numbers? Follow this complete guide to streamline billing while staying secure and com...
December 30, 2025

Service Invoice Examples in Various Business Sectors
Not sure how to create a proper invoice? Learn the right service invoice format, its key functions, and common mistakes to avoid.
December 29, 2025

Vendor Management System: The Key to Efficient Vendor Operations
Explore what a vendor management system is, how it works, and real-world examples to manage vendor operations more efficiently and with bet...
December 26, 2025

Vendors Explained: Their Role and Types in Modern Business
Vendors are an essential part of any business partnership. Learn their definition, roles, types, and the key legal and contractual aspects....
December 25, 2025

Tax Consultants Explained: Their Roles, Duties, and Challenges
Learn about tax consultants, their roles and responsibilities, and the ethical standards they must uphold when assisting taxpayers.
December 24, 2025

Tax Payment Codes: A Complete Guide to Avoid Payment Errors
Mistakes in tax payment codes can result in costly penalties. Learn their purpose, common examples, and how to avoid the risks.
December 23, 2025
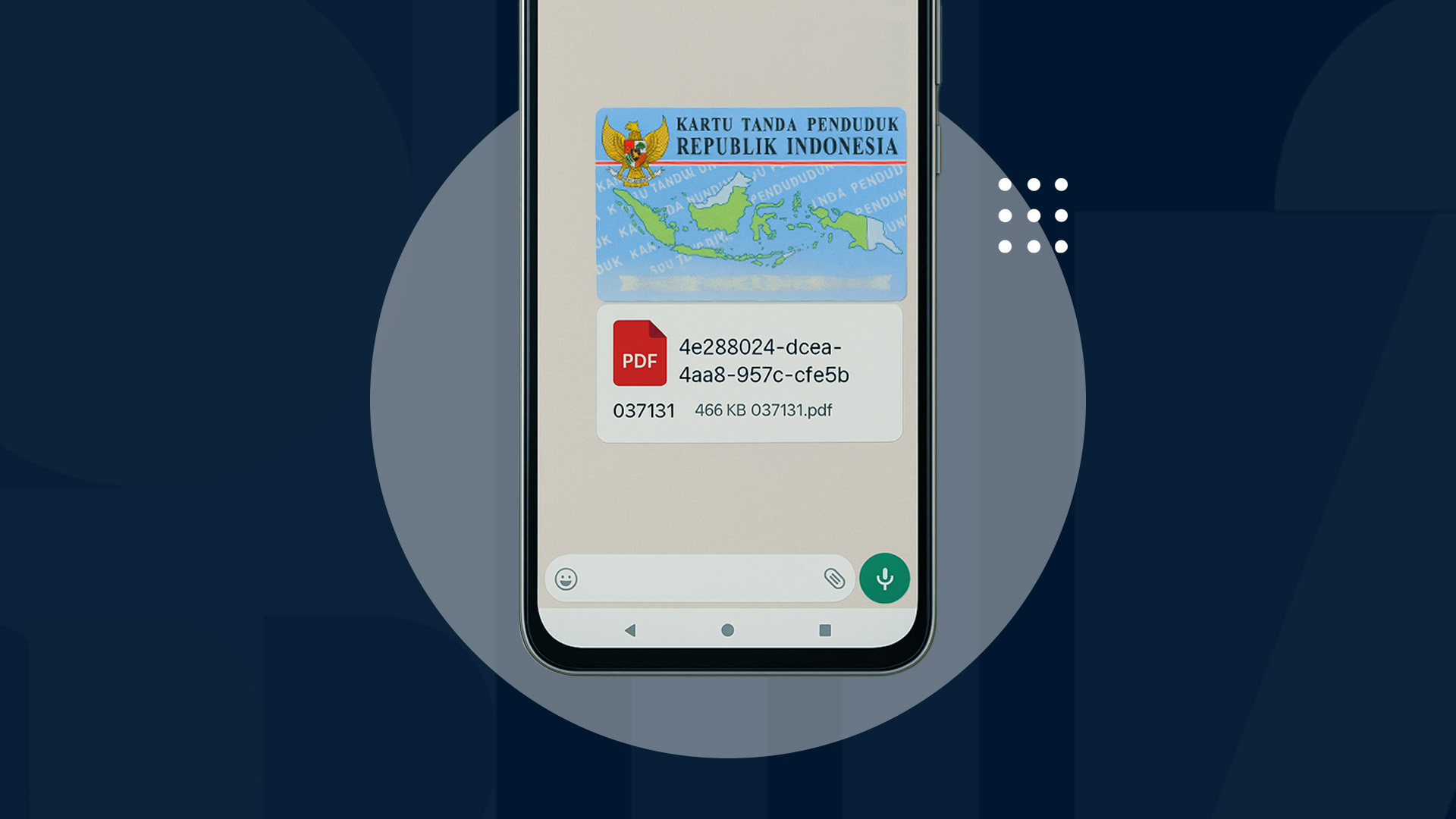
How to Send a PDF on WhatsApp and How Safe It Really Is
Learn how to send PDF files via WhatsApp from your phone or laptop. Understand the risks of document theft and how to protect your importan...
October 24, 2025

Biometric Liveness: What It Is and Why It Matters for Identity Security
Biometric liveness technology ensures that identity verification is performed only by real humans—not deepfakes. Learn how it works and why...
October 24, 2025

Fake ID Cards: Types of Scams and How to Avoid Them
Fake ID scams have become increasingly common. It’s important to understand the types of fraud, how they work, and how you can protect your...
October 21, 2025
.jpg)
KYC: What It Is and How It Protects Your Identity
KYC is the process of verifying a user’s identity to guard against digital fraud. Why is it necessary—and why should you care? Let’s explor...
October 20, 2025

Liveness Detection: Telling Humans Apart from Deepfakes
Advanced technology like liveness detection can distinguish real faces from deepfakes. Take action now—protect your identity and stay ahead...
October 18, 2025

Free Online Signatures: Are All Websites Legal?
Find out whether all free digital signature services are actually legal. Learn the differences and discover solutions that are officially r...
October 14, 2025

Coretax Tax Invoice: Guide, E-Signature, and Digital Certificate
Learn how to easily create complete tax invoices in Coretax, including how to apply digital signatures, electronic certificates, and DJP au...
October 10, 2025

Forgery of Digital Signatures: Legal Provisions and Penalties
Understand the legal foundations surrounding signature forgery, the criminal sanctions involved, and how to prevent it using certified digi...
October 04, 2025

Examples of Personal Data Most Easily Stolen by Hackers
Be aware of the types of personal data—such as your name, national ID number (NIK), email, and more—that hackers can steal easily. Learn wh...
October 04, 2025
Got a Question?
We're Here to Help!

