10 Digital Fraud Cases Consumers Need to Watch Out For
Be aware of the most common online fraud cases such as phishing, SIM...
Learn about the different types of taxes in Indonesia, their benefits, and how Coretax supports secure, integrated tax reporting.
February 11, 2026
AI-powered attacks—such as large-scale deepfake attacks, synthetic identity fraud, and automated device farms—are effectively eroding trad...
February 03, 2026

Be aware of the most common online fraud cases such as phishing, SIM...
July 30, 2025

Financial fraud in the Philippines is rising fast. Learn how identity...
July 28, 2025

Learn the official requirements, fees, and tips for handling an Umrah...
July 22, 2025

Learn about different types of partnership agreements, the key...
July 21, 2025
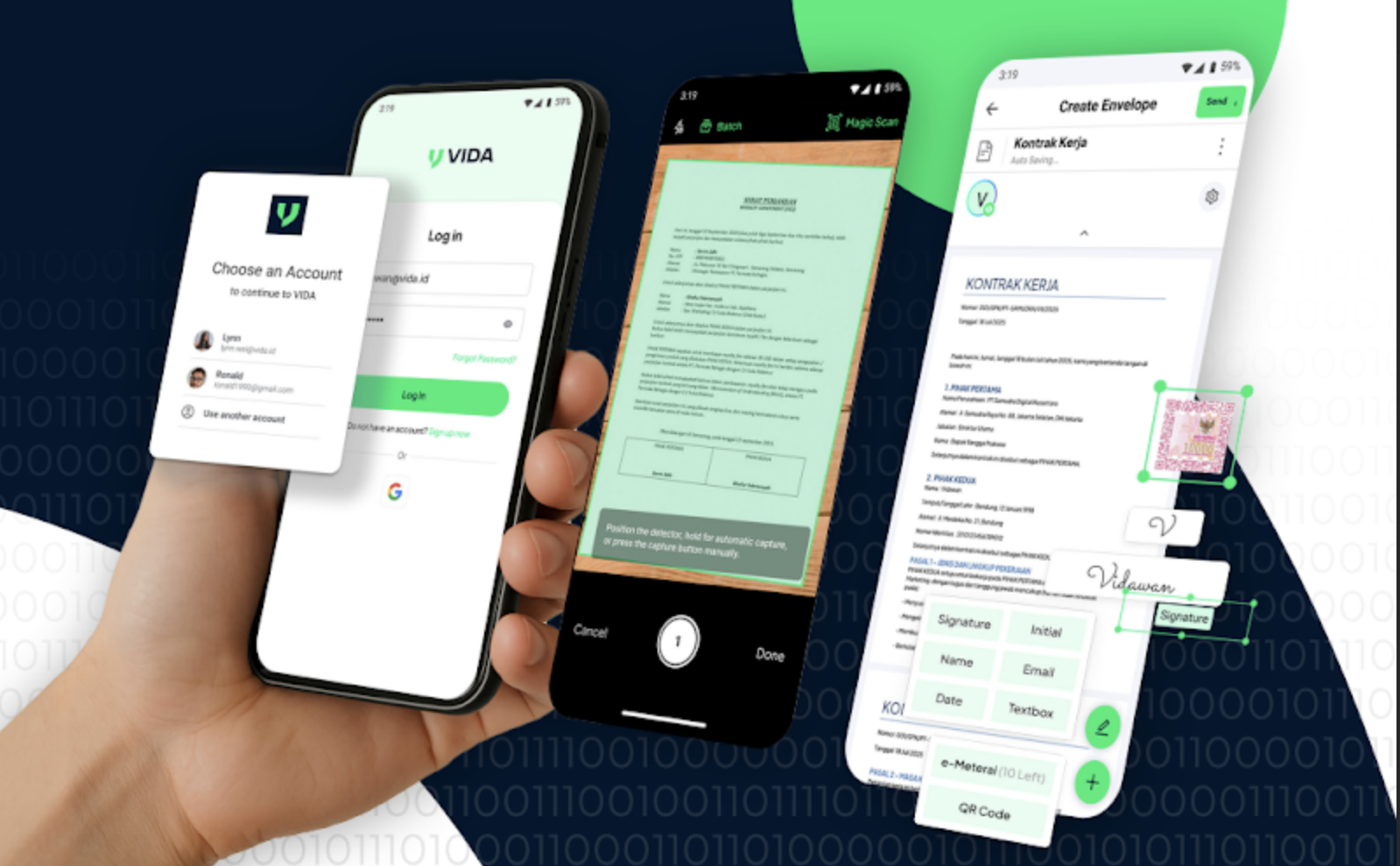
Just got accepted at a new job? Take a look at sample employment...
July 20, 2025

Ready to sign your employment contract? Learn the types of contracts...
July 16, 2025

Learn about the latest fraud cases that exploit AI, APK files, and...
July 16, 2025

Understand the difference between initials and signatures so you...
July 14, 2025

Manage car rental business documents quickly and neatly. Scan,...
July 13, 2025

Want to start selling online on TikTok and other popular e-commerce...
June 30, 2025

Effective tips to stop phishing from checking suspicious links,...
June 29, 2025

Be aware of various online scams from phishing and loan fraud to...
June 26, 2025