Recently, headlines exploded with the news that “16 billion passwords have been leaked to the public.” Imagine, 16 billion passwords leaked means two compromised accounts per person on average.
These leaked passwords can be misused by cybercriminals to access your digital accounts or launch chain fraud schemes. This leak isn't just a one-time incident—it’s a compilation of old breaches gathered together, involving countless victims over the years.
It's time we acknowledge that passwords are a major security threat. To stay safe, we must rethink how we log in.
This Isn’t the First Time
Cybernews, the platform that broke this story, explained that the 16 billion credentials came from 30 separate data compilations, each containing between 10 million and 3.5 billion records. The sources include:
-
Infostealer malware logs
-
Credential stuffing databases
-
Leaked tokens, cookies, and session IDs
What’s more alarming: some of the leaks include data that can bypass multi-factor authentication (MFA).
A Cybernews researcher stated,
“This dataset is dangerous because it combines old and new logs from data-stealing malware, including session cookies and tokens. If companies don’t use strong authentication, the risk is huge.”
This makes credential leaks an open invitation for cyberattacks like phishing, account takeovers, ransomware, and business email compromise (BEC).
Real Threats from Password Leaks
-
Credential Stuffing
Hackers try stolen username-password pairs on multiple sites. If you reuse passwords across accounts, one leak can give attackers access to everything—from your email to your online banking. -
Account Takeover
Once hackers gain access to your credentials, they lock you out and hijack your accounts. -
Ransomware & BEC Attacks
On a company level, leaked credentials can let hackers spread ransomware or impersonate execs to scam the finance team into transferring money to fake accounts. -
Bypassing MFA
Some leaks include session tokens that allow logins without needing OTPs. This defeats even two-factor authentication.
What Should You Do?
-
Check If Your Data Was Leaked
Visit HaveIBeenPwned.com or Cybernews Leak Checker to see if your email or password has been compromised. -
Stop Reusing Passwords
Use a unique, strong password for every account. A password manager can help. -
Enable Multi-Factor Authentication (MFA)
MFA adds another security layer, even if your password is compromised. -
Switch to Passkeys
Many platforms now support passwordless login using passkeys, which rely on cryptographic keys stored on your device. Simply use your fingerprint or face to log in—no typing required.
Passwords Are Outdated, So What’s Next?
The password era is over. They’re easy to guess, steal, and misuse. If your company still relies on passwords, here’s what that means:
-
Customer accounts remain vulnerable
-
Data breach risks stay high
-
Users don’t feel secure during login
To gain trust, companies must shift to passwordless login.
VIDA’s Solution: Secure Login for Regulated Industries
VIDA, a certified digital authentication provider in Indonesia, offers two powerful solutions based on the same cryptographic backbone as passkeys:
1. VIDA PhoneToken: Cryptographic Keys in Your Phone
Instead of OTPs or passwords, your account is cryptographically linked to your device via Public Key Infrastructure (PKI).
-
Private key stays in your phone’s secure enclave
-
Each login is cryptographically signed
-
Only your registered phone can be used to log in
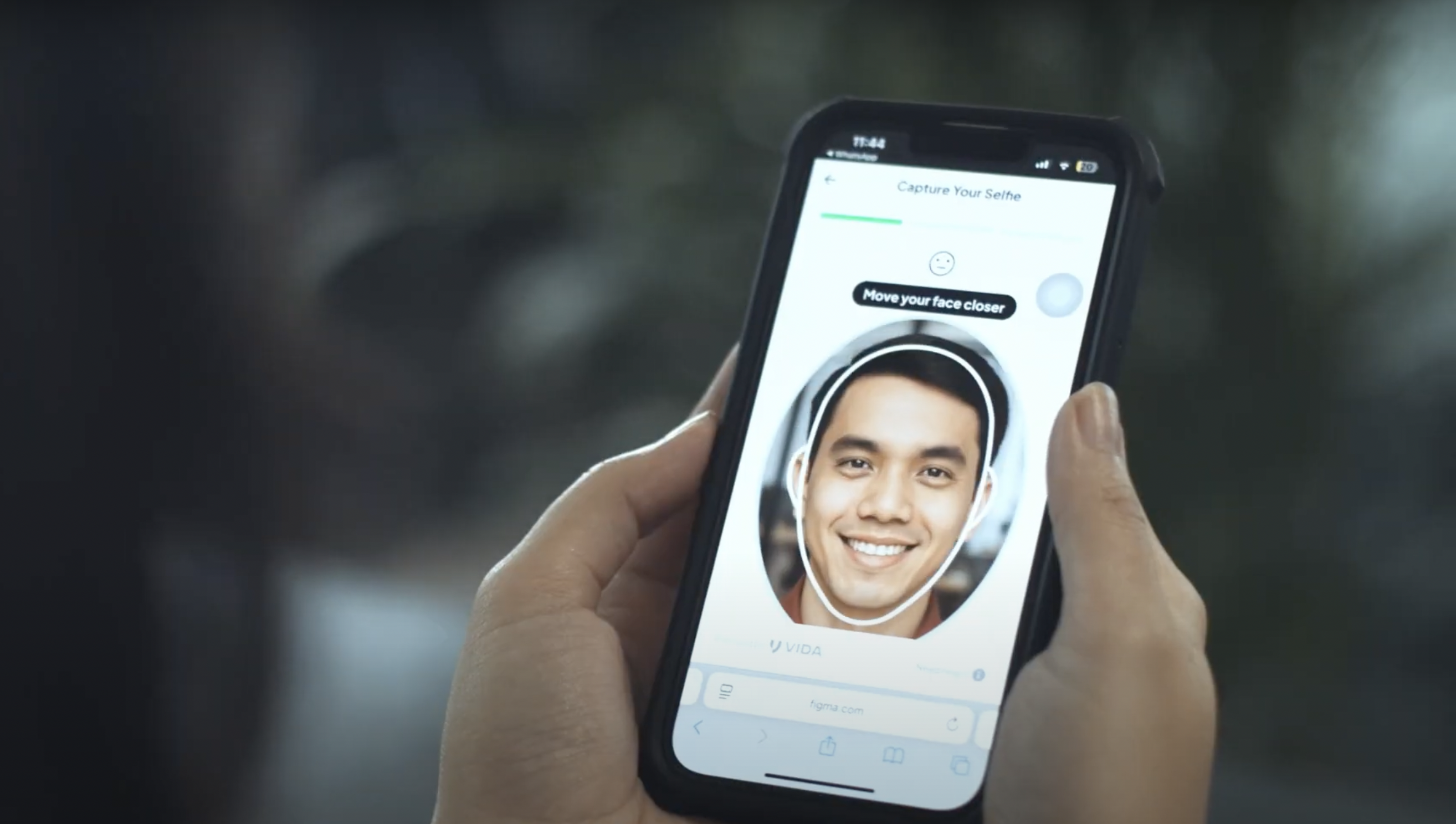
2. VIDA FaceToken: Log In with Your Real Face
FaceToken uses facial recognition combined with liveness detection to ensure only your real, live face can authenticate.
-
Compares with verified biometric data
-
Passive liveness check (blinks, slight movement)
-
Fast, seamless login, no typing required
Together, PhoneToken and FaceToken enable passwordless, OTP-free login that’s fast, secure, and phishing-proof.
The real issue isn’t just that data has leaked today—but what cybercriminals might do with that data tomorrow.
Learn more about VIDA PhoneToken and FaceToken here.
.png)

.jpeg)
