What's Fraud Triangle and How It Happens
Fraud triangle adalah konsep untuk memahami bagaimana fraud bisa...
Learn about the different types of taxes in Indonesia, their benefits, and how Coretax supports secure, integrated tax reporting.
February 11, 2026
AI-powered attacks—such as large-scale deepfake attacks, synthetic identity fraud, and automated device farms—are effectively eroding trad...
February 03, 2026

Fraud triangle adalah konsep untuk memahami bagaimana fraud bisa...
July 06, 2024

Fraud is an act of deception that harms individuals or companies....
July 05, 2024

Security awareness is important for both individuals and companies....
July 04, 2024
.jpg)
Injection attacks occur when an attacker injects malicious code or...
June 25, 2024

Personal data protection in Indonesia is regulated under the Personal...
June 25, 2024
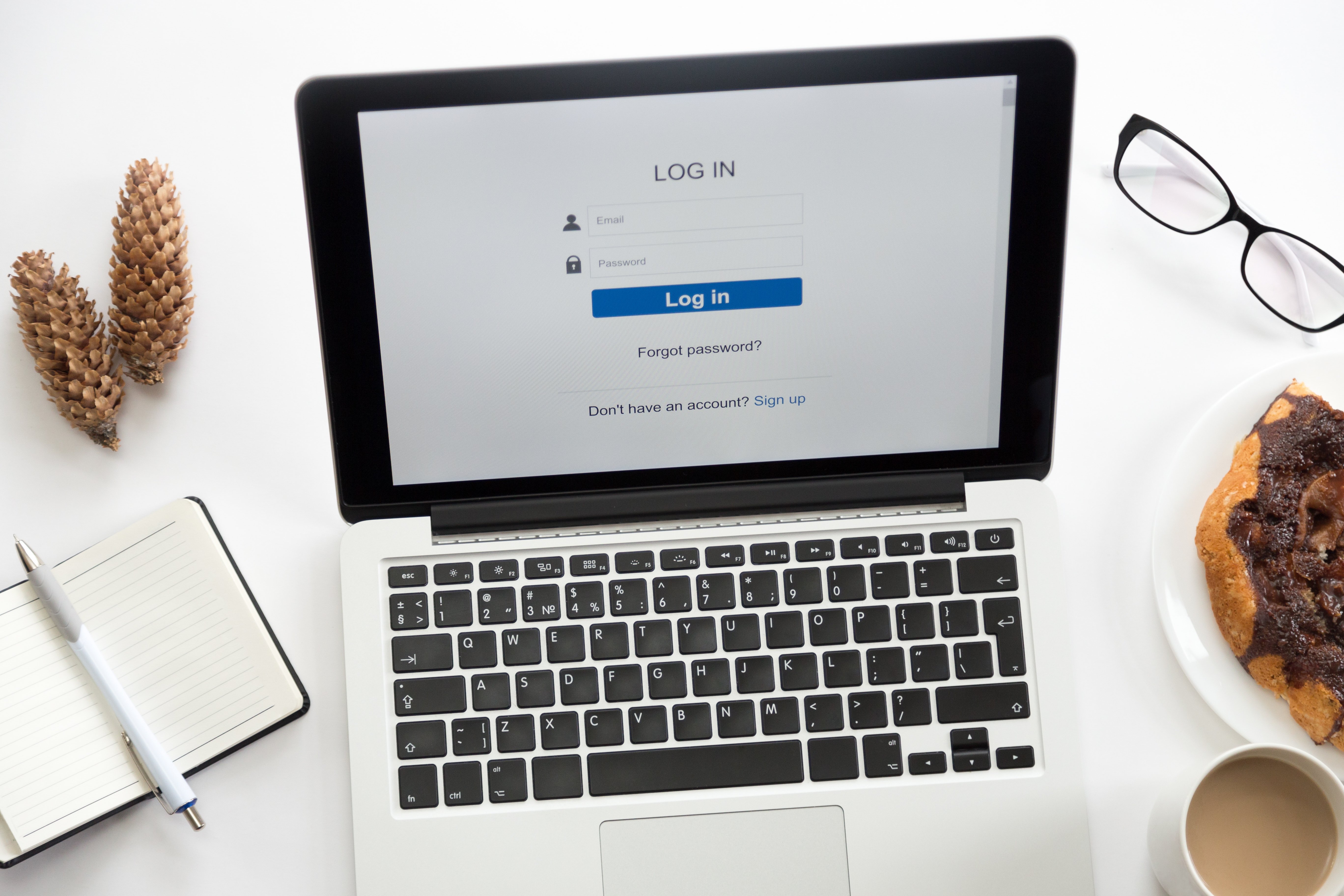
Personal data is data that identifies an individual in physical or...
June 24, 2024

The development of the internet has brought numerous benefits to...
June 23, 2024

Hackers and crackers are two main actors in the world of cybercrime....
June 14, 2024

Hackers are cyber criminals who target network security systems. What...
June 14, 2024

Cyber security is security applied in the internet-connected world....
June 14, 2024

Indonesia has experienced a significant increase in cyber attacks....
March 18, 2024